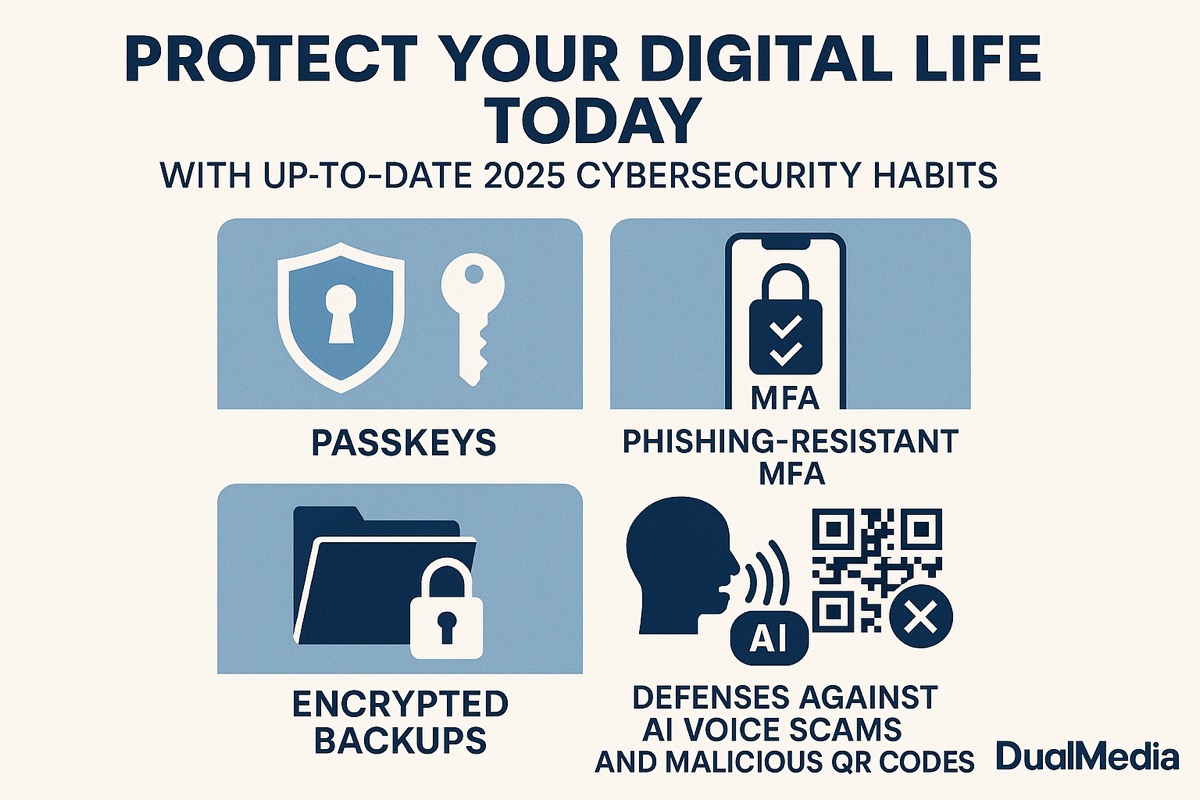
Protect your digital life today with up-to-date 2025 cybersecurity habits with DualMedia —passkeys, phishing-resistant MFA, encrypted backups, and defenses against AI voice scams and malicious QR codes.
Exploring the Latest Technology Trends in Web Development
Envision an escalator, perpetually ascending. The ceaseless steps, representing the relentless forward movement of technology, are continuously shaping our existence, be it personal or professional, intimate or social. We’ve borne witness to a myriad of innovations, from the handheld marvels of smartphones to the nebulous expanse of cloud computing, that have indelibly imprinted on virtually
Are Your Cybersecurity Tools Keeping Your Data Safe?
Ensure the effectiveness of your cybersecurity tools in protecting your data. Learn key factors to consider and evaluate their performance in this post. In today’s interconnected world, where data breaches and cyber threats are on the rise, ensuring the safety and security of your sensitive information has become more important than ever. With numerous cybersecurity
VoIP Hosting services for Business
Exploring the Viability of VoIP Hosting Services for Your Business In the rapidly evolving landscape of modern business communications, the utilization of VoIP Hosting Services for Business has gained unprecedented traction. However, it is incumbent upon us to recognize that these services might not universally align with every organizational or individual requirement.
Ransomware Attack News: The Growing Cyber Menace
Ransomware attack incidents are surging worldwide, threatening businesses and individuals alike. Learn the latest trends, real-life cases, and essential strategies to protect against this growing cyber threat.
Crypto Security and Privacy: Protect Your Digital Wealth Today
Crypto security and privacy are critical for protecting digital assets. Discover effective strategies, tools, and tips to safeguard your cryptocurrency investments today!
Cloud Security News: Protecting Data in the Digital Cloud
Protecting data in the digital cloud is vital in today’s interconnected world. Discover best practices, emerging technologies, and strategies to safeguard your cloud data effectively.
Mobile Payment Technology: Transforming the Future of Commerce
Mobile payment technology is revolutionizing digital transactions. Discover its innovations, benefits, and how it’s shaping the future of commerce.
Top 10 Cybersecurity Tips to Stay Safe Online
Stay secure online with these Top 10 Cybersecurity Tips. From strong passwords to software updates, learn how to protect your data and stay ahead of cyber threats.
Think Your Online Identity Is Safe?
Ensure your online identity is safe with these essential cybersecurity tips. Learn how to protect your digital presence from hackers and evolving threats.
Protect Yourself from Cyber Threats: Avoid These 5 Common Cybersecurity Mistakes
Protect your valuable information by avoiding these 5 common cybersecurity mistakes. Learn how to secure your accounts, stay safe on public Wi-Fi, and back up your data effectively.
Are Hackers Secretly Controlling Your Smart Devices?
Are hackers secretly controlling your smart devices? Learn about the growing concern of unauthorized access to smart devices and how to protect your privacy and security. In this article, we shed light on a growing concern that may be lurking within your smart devices – the secret control of hackers. As our lives become increasingly
Are You Safe? The Shocking Cybersecurity Secrets Revealed!
Discover the shocking secrets of cybersecurity threats and vulnerabilities, and learn how to protect your personal data from cyber attacks. Safeguard your online presence now! In a digital era where personal information is more vulnerable than ever before, ensuring cybersecurity has become a paramount concern. This article explores the shocking secrets behind the safety of
Is Your Business Vulnerable To Cyber Attacks? Find Out Now!
Is your business vulnerable to cyber attacks? Learn about key indicators and steps to enhance your cybersecurity defenses in this informative article. Safeguard your valuable assets now! As technology continues to advance, so do the threats posed by cyber attacks. It is becoming increasingly crucial for businesses to evaluate their vulnerability to these attacks and
Is Your Personal Data At Risk? Cybersecurity Experts Warn Of New Threat!
In today’s digital age, the safety and security of our personal data have become more critical than ever before. With countless cyber threats and sophisticated hackers constantly lurking in the shadows, it is essential to remain vigilant and proactive in safeguarding our valuable information. Cybersecurity experts have recently sounded the alarm on a new threat
Are You Safe Online? The Shocking Truth About Cybersecurity Threats Revealed!
Discover the shocking truth about cybersecurity threats and learn how to protect yourself online. Stay safe from malware, phishing, ransomware, and social engineering attacks. Understand the global rise in cyber attacks and financial losses due to cybercrime. Get valuable tips for individuals and businesses to enhance their cybersecurity measures. Explore the role of government in
Is Your Cybersecurity Putting You At Risk? Find Out Now! – DualMedia Innovation News
In today’s interconnected world, the importance of cybersecurity cannot be emphasized enough. As an individual, it is crucial to ensure that your personal data and online activities are adequately protected from potential threats. That being said, have you ever wondered if your current cybersecurity measures are truly safeguarding you or if they are leaving you
Cybersecurity Careers: Opportunities in a Growing Industry
In the continuously intertwining threads of our world and technology, the call for individuals versed in cybersecurity continues to amplify. Just as cyberspace constantly shifts and evolves, the field of cybersecurity adapts, presenting a myriad of roles and specializations. Allow us to lead you on a tour through the captivating universe of cybersecurity professions, shedding
IoT Innovations: Transforming Connectivity and Efficiency
The Internet of Things (IoT) is orchestrating a radical metamorphosis in our everyday living and working patterns. It’s an arena where connected devices and systems are reshaping industries, carving out fresh avenues. This narrative will take you on a journey through the recent developments in IoT and their transformative influence on connectivity and efficiency. IoT
Crypto Exchanges: Latest News and Industry Developments
In the heart of a digital revolution, there lay crypto exchanges: bustling, dynamic platforms forging connections in the cryptosphere where cryptocurrencies are exchanged like secrets in the night. They serve as the lifeline of this ecosystem, bridging the gap between traditional finance and the thrilling, unpredictable world of cryptocurrency. Today, we explore the ever-shifting landscape
Cybersecurity Industry: Tracking Market Trends and Growth
In the labyrinthine universe of technology, an industry is rapidly taking center stage. This formidable protagonist is none other than cybersecurity, a realm that safeguards our digital worlds from clandestine predators seeking to shatter our data sanctity. This piece aims to unfold the ever-expanding tableau of cybersecurity, meandering through the industry’s growth narrative, pioneering technologies
IoT Security News: Safeguarding Connected Devices
A kaleidoscopic assembly of devices – whether they be physical entities, automotive marvels, or towering buildings – finds itself woven into the intricate network we fondly term the “Internet of Things” (IoT). Layered with sensors and laced with advanced software, their communicative abilities overflow. They drink in vast quantities of data only to spew them
Cybersecurity Tech Updates: Strengthening Digital Defenses
As we hurl ourselves headlong into the undulating waves of technological advancement, the specter of cyberattacks looms, magnifying with our escalating reliance. A chameleonic enemy, cybercriminals continually metamorphose, devising innovative stratagems to infringe upon vulnerabilities, pilfering invaluable information. Enter the theatre of cybersecurity – a ceaseless battlefield where valiant protectors of digital realms vigilantly guard
Malware and Virus Updates: Threats Lurking in Cyberspace
Immerse yourself in the intricate tapestry of our digital lives, stitched meticulously by the internet’s ceaseless loom. It has wrought a world revolutionized beyond recognition, yet it is not devoid of shadows. Among these shadows lurk malware and viruses, threats that beleaguer us with relentless frequency. Come, join me on a voyage through the labyrinth
Data Breach News: Uncovering the Latest Cyber Incidents
In our modern existence, the specter of data breaches is ubiquitous, insidious in its commonality. The ethereal dimension, the electronic world, the internet, is a battlefield. Confronted by shadowy figures of cybercrime, they continue to devise ingenious ways to illicitly obtain sensitive data from unsuspecting individuals and corporations. The ensuing narrative takes a deep dive
The Rise of Privacy-Focused Technologies
In a world that trembles, teetering on the verge of virtual vulnerability, the invisible undercurrent of digital privacy threats, those looming specters of cyberattacks, the chilling onslaught of data breaches, and that peering, intrusive eye of surveillance practices, steadily proliferates. This eerie scenario, all too real and increasingly commonplace, echoes a resounding call, a veritable
The Impact of the Internet of Things (IoT) on Cybersecurity
Picture this: everyday objects around you, whispering to each other in a language only they understand, exchanging data, and making decisions. That’s right, we’re talking about the Internet of Things (IoT), the unseen conductor of our symphony of progress. Oh, how it’s reshaped our existence, making us both spectators and participants in a dance where
Best Wireless Security Cameras 2023
Ultimate Guide to the Top Wireless Security Cameras of 2023: A Comprehensive Review In the current year of 2023, the ever-expanding market has reached its saturation point with an overwhelming abundance of wireless security cameras. These innovative devices have been specifically engineered to safeguard and closely observe your residential abode. What sets these cameras apart
Top 10 Technologies You MUST Learn In 2023 – Upcoming Technologies That Will Change the Game!
The Future of Tech: Skills You Need to Stay Relevant and In-Demand. Embarking upon this informative blog post, let us delve into the captivating realm of top trending technologies that have not only gained popularity in the year 2023 but are poised to sustain their demand well into the future. These groundbreaking technologies are of
5 Tech Innovations Disrupting the Business World
In this perpetually shifting landscape of business, the unrelenting and indomitable force of technology relentlessly continues to reshape and redefine our operational paradigms, challenging the very foundations of conventional models and incessantly pushing the boundaries of innovation. To maintain an unparalleled competitive edge amidst this ceaseless flux, businesses must incessantly strive to stay not one,